A HIPAA Compliance Tool…plus so much more! |
|
|
|
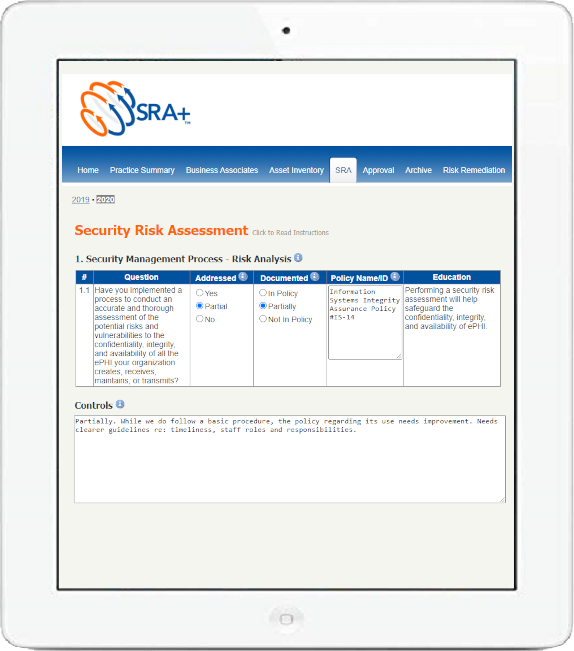
How Does it Work?
In this step-by-step program, the HIPAA Security Rule’s implementation specifications for administrative, physical, and technical safeguards are introduced one at a time, and questions are asked to help the user assess how their organization addresses each one. As weaknesses are discovered, they are linked to identified vulnerabilities which, if exploited by various threats, could impact the privacy, integrity, and availability of electronic protected health information (ePHI). These risks are then ranked based on their likelihood and impact, providing your organization’s security team an actionable list of items to examine, and then plan, implement, and document their remediation activities accordingly.
Why do I need more than just the SRA?
Properly documenting this year’s remediation activities leads right into next year’s SRA. It’s a process that never really ends. SRA+™ makes it easy to navigate through the process, always knowing where you are and what you should do next. Perhaps the best part: you don’t have to do it alone. Safeguarding your patients’ data may sometimes require expertise beyond your usual scope of practice. Contact us for more information.
KFMC Health IT consultants bring a thorough understanding of the laws that govern the protection of patient information and the ability to assess the security of your PHI, the effectiveness of your processes, and your compliance with the HIPAA Security Rule.